The shift to remote work has not only increased Internet traffic. It has also caused a spike in cyberattacks. While all types of assaults upsurged in 2020, ransom attacks prevailed. They rose by 150% over the previous year. Along with this, the sum paid by victims grew by over 300%.
In 2025, this trend is not decreasing but growing. Who usually becomes a victim of cyberattacks? High-profile ransom cases are making daily headlines, engaging individuals, critical infrastructure, private companies, and municipalities. And online retailers are not an exception.
Hackers demand more, extending their requirements to tens of millions of dollars. They capture essential company data and keep it hostage in exchange for cash, making the attacks more complex.
How can an eСommerce business protect itself from cyberattacks? First of all, you need to monitor changes and update your tools constantly.
I can provide an example of Magento 1 to Magento 2 migration challenges. In 2020, the company stopped supporting Magento 1. So stores on Magento 1 no longer receive new security updates. It puts their business at risk.
Regardless of the platform you use as the basis of your store, you need to develop an eCommerce security plan. And use special tools dedicated to protection against threats. Here, I collected an overview of ten essential tools to integrate.
10 Cybersecurity Tools for eCommerce You Need to Utilize
What happens when you face an attack unprepared? It’s not only about losing money. It’s a reputational loss too. Simply put, you need to nurture customer trust in your products and business and protect them.
That’s why you need these cybersecurity tools. They’ll help you fight hackers and protect your customers’ personal and financial information, such as:
- credit or debit cards (or other payment info);
- emails;
- phone numbers,
- and other information.
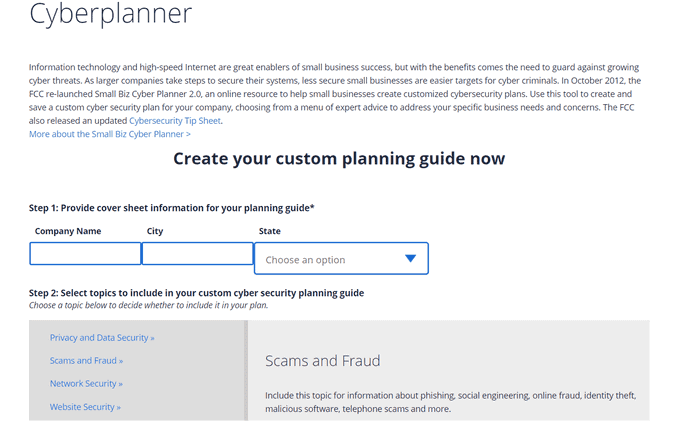
1. FCC Small Biz Cyberplanner
Screenshot taken on the official Federal Communications Commission website
What is the Small Biz Cyber Planner? It’s a free online resource created by the Federal Communications Commission. It assists small businesses in developing tailored cybersecurity plans.
How do you do it? You select from a menu of professional recommendations to address your individual business needs and concerns.
The product appeared as a result of an unprecedented public-private partnership between government experts and private IT and security companies, including:
- DHS;
- NIST;
- The US Chamber of Commerce;
- The Chertoff Group;
- Symantec;
- Sophos;
- Visa;
- Microsoft;
- HP;
- McAfee;
- among others.
It first went live in October 2011 and was relaunched in 2012.
The Cyber Planner 2.0 includes:
- information on cyber insurance to help mitigate business interruptions and financial losses caused by cyber-attacks;
- best practices on spyware, such as avoiding advanced versions of spyware and what to do if infected;
- recommendations to install new software systems that enable remote cleaning and tracking of laptops and mobile devices.
In addition, the FCC has revised its one-page Cybersecurity Tip Sheet. It’s a quick resource with suggestions on building a mobile device action plan, as well as payment and credit card security.
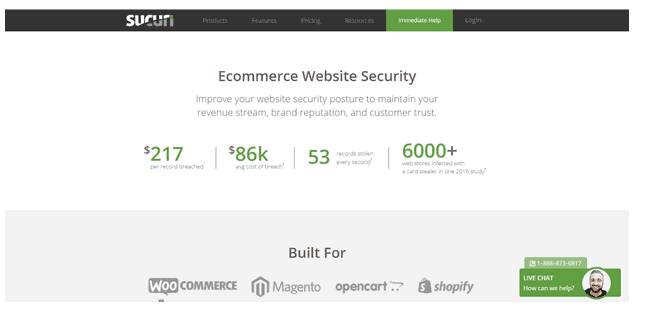
2. Sucuri
Screenshot taken on the official Sucuri website
Sucuri Website Security Platform is a service that protects websites from any threat. How does it work? It redirects traffic through the Sucuri servers. There, it checks every incoming request to the site and blocks them if there are apparent suspicions.
But does it reduce the site’s speed, you ask? No, it doesn’t. When the detected malicious request is blocked, everyone else proceeds without problems. Moreover, it increases the site’s uptime because requests go to a third-party Sucuri server and reduce the site’s server load.
Also, the Sucuri Website Security Platform optimizes your website to work faster. Here is how it ensures it:
- It copies the pages to the branded CDN Anycast site.
- When receiving the request, it presents the copy on the nearest Sucuri server to the user.
Suppose the hacker still managed to break through the protection. In that case, the Sucuri Website Security Platform will find the site’s vulnerability that failed to stop the attack. And eliminate it free of charge.
Sucuri is now a Level 1 PCI Compliant Service Provider, thanks to Sucuri Firewall. It’s a proprietary virtual patching and hardening technology. The firewall conducts its function by enclosing your website in a secure defense system.
Sucuri also contains an Intrusion Prevention System (IPS), which protects against all types of website security threats. It defends any credit card data flowing through its channels, which complies with PCI-DSS requirements.
Let’s Encrypt’s free SSL certificates encode your customers’ data and protect them in transit. Sucuri also supports your certificates if you have them.
Furthermore, Sucuri integrates with various popular eCommerce platforms, including
- WooCommerce;
- Magento;
- Shopify;
- Opencart;
- and others.
The security service will cost you from $199.99 up to $499.99 a year with all the advanced features.
3. Astra
Screenshot taken on the official Astra website
Astra Security Suite is an intuitive control panel. It covers Web Application Firewall (WAF), malware scanners, and security auditing. In addition, you can install a ready-made GDPR consent code snippet. It defended major brands such as Gillette, African Union, Ford, Carrier, Oman Airways, Hotstar, Kotak Bank, and Akeneo.
Astra protects your site from the following issues:
- OWASP Top 10 Web Application Security Risks;
- credit card hacking;
- phishing attacks;
- spam by email;
- SEO spam;
- unwanted traffic;
- etc.
It ensures 100% safe checkouts for e-stores. As such, Astra eCommerce Suite includes:
- The Intelligent Firewall. It protects your website from XSS, SQLi, spam, malicious bots, and 100 other dangers. It also ensures that only real people can access your website.
- Malware Scanner. It’s an autonomous, machine learning-powered tool. Malware Scanner is available 24 hours a day, seven days a week, allowing you to search your site for dangerous elements whenever you wish. It can automatically scan your site daily, weekly, or monthly. You will see the results in your dashboard, along with a list of flagged files and cleaning recommendations.
Astra is fully compatible with CMS, such as:
- WordPress;
- Magento;
- Opencart;
- Prestashop;
- Drupal;
- so on.
The great thing about it is that Astra frees you from long forms with infinite fields and expensive setup processes. You’ll need less than five minutes to protect the most sensitive data on your eCommerce website. It provides human help and complete guidance at every step of an already simple setup process.
To get the service, you need to pay $24 per month.
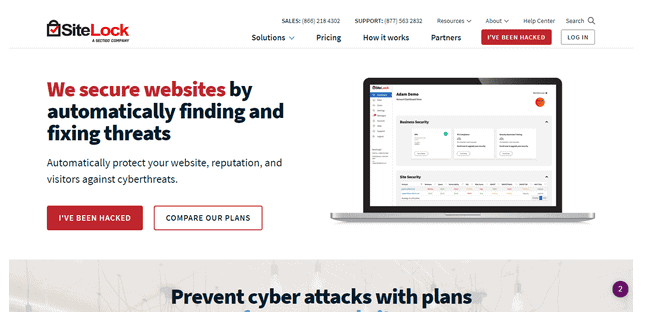
4. SiteLock
Screenshot taken on the official SiteLock website
SiteLock is a cloud-based and cost-effective way to protect your business and reputation against hackers, including:
- scanning websites around the clock;
- defending against security threats such as malware, cross-site scripting (XSS) assaults, bots, and SQL injection;
- keeping track of blacklists;
- fixing all of your CMS vulnerabilities.
SiteLock uses a content delivery network (CDN) to boost your site’s speed by up to 50%.
Its primary purpose is to safeguard your most valuable asset: your clients. The solution detects and prevents any harmful or suspicious behavior on your eCommerce website. It provides automated alarm emails and a real-time security dashboard.
If you use SiteLock, you can display its Trust Seal on your website to boost client confidence. SiteLock’s eCommerce protection is also PCI-compliant. It means your clients’ payment information will remain safe from fraudsters.
How does it affect your business? People see the transactions will be secure. So it instantly translates into higher conversions for your company. Plus, these solutions increase the performance of your website and optimize your SEO strategy.
The pricing plans start from $14.99 a month.
5. Cloudflare
Screenshot taken on the official Cloudflare website
Cloudflare is a server network. A web application firewall in Cloudflare’s suite prevents SQL injection and cross-site scripting threats. It also uses TLS 1.3 to encrypt all customer transactions and sensitive data, which aids in the PCI-DSS certification process.
You know there can be expected traffic spikes. They happen during seasonal shopping events. However, this traffic can also mean you experience distributed denial of service (DDoS) attacks. Therefore, it’s vital for your eCommerce website to detect them.
Cloudflare for eCommerce avoids outages caused by large-scale DDoS attacks and provides load balancing to spread traffic. You can also manage DNS records on the domain and transfer the site to HTTPS.
Cloudflare has a free plan and three premium options starting from $20 monthly. They determine the level of protection and possibilities for speeding up the site.
How does it accelerate site loading? It’s all because of CDN technology. Simply put, Cloudflare caches static files from your site, such as images, CSS, Javascript, etc., on its servers around the world.
Then it distributes them from servers that are closer to visitors. It reduces the load on the hosting and the distance the data travels.
DDoS protection, in turn, works because all incoming traffic first passes through Cloudflare, as if through a filter. The company analyzes incoming traffic, blocks suspicious requests, and sends the legitimate ones to your website.
6. Datadog
Screenshot taken on the official Datadog website
Datadog is a monitoring service for IT departments that unites massive amounts of data into a single view of the IT infrastructure.
The Datadog SaaS platform enables multiple teams to collaborate on infrastructure issues. For example, Datadog ties together metrics and events from every component in the environment. How does it assist businesses? It lets teams graph, correlate, and analyze data.
Datadog has a Cloud Security Platform. It provides a robust security monitoring solution for the cloud age.
To strengthen its capabilities, the company has acquired Sqreen this year. What is Sqreen? It is a SaaS security platform. It analyzes your app in real-time to detect vulnerabilities in your code or configuration. It also allows you to forget about manual interference when your application stack changes because Sqreen safeguards adapt to it.
So, Datadog will now continue to provide even better eCommerce security. The service cost starts from $0.20 per GB of analyzed logs per month if billed annually or $0.30 on-demand.
7. GnuPG
Screenshot taken on the official GnuPG website
GnuPG is a free, open-source command-line program. It’s an application for encrypting data.
It evolved from the previous Pretty Good Privacy encryption standard (or PGP). GPG leverages the OpenPGP standard to define the canonical format for encrypting messages, certificates, and signatures using a public key exchange.
How does it secure communication? It uses a unique personal key that identifies the data’s owner and provides protection against tampering. It also has a flexible key management system and multiple access modules for a variety of public key directories.
Encryption is a great way to secure communications between two parties while quickly sending sensitive data over an insecure network.
8. Check Point Software Technologies
Screenshot taken on the official Check Point Software Technologies website
Check Point Software Technologies is one of the leaders in the cybersecurity industry. The company has existed for over 25 years and strives to ensure the reliable operation of its clients’ information products.
The company’s management identifies six generations of cyber threats:
- The first generation emerged in the late 1980s. These virus attacks have affected businesses and led to the development of antivirus solutions.
- The second generation emerged in the 1990s. These are cyberattacks from the Internet space requiring the installation of a firewall.
- The third generation appeared in the 2000s to detect application vulnerabilities. Intrusion Prevention Systems (IPS) came out to protect against such attacks.
- The fourth generation, which emerged in 2010, required creating behavior analysis technologies such as sandboxes.
- The fifth generation appeared in 2017 when threat detection was no longer enough. Combating this generation of cyber-attacks requires advanced threat prevention technologies.
- The youngest, sixth generation, which appeared only in 2019-2020, consists of numerous cyberattacks on IoT devices with outdated firmware. To combat this threat, you can use nano-security agents, that is, micro-plugins that can control all data coming in and out of the IoT network element.
Most companies have protection from only 1-3 generations. Check Point Software Technologies solutions, in turn, can withstand all of the above generations of cyberattacks.
Check Point Infinity’s new consolidated architecture can detect and remediate Layer 5 and 6 cyberattacks across all networks, endpoints, clouds, workspaces, and IoT that are part of a customer’s infrastructure.
The company provides automated network, mobile, and Cloud Security Posture Management (CSPM). It ensures PCI-DSS and regulatory compliance, securing digital transformation and customer experience.
To find out the cost of the solution, you need to contact the sales department. You can also request a demo or try it for free.
9. Splunk
Screenshot taken on the official Splunk website
Splunk collects and analyzes machine data. These data are called logs. There are numerous solutions to store data on the market. But what sets Splunk apart?
One of the platform’s main features is that it can work with data from almost any source. Therefore, the list of possible applications of the system is extensive.
Splunk, in most cases, parses the input data into fields, values, and then processes them. It takes place through SPL queries (a particular Splunk language).
It provides you with various possibilities, including:
- building selections and tables;
- sorting, filtering, aggregating;
- writing reports;
- creating calculated fields and dashboards with a broad spectrum of visualization;
- accessing both internal and external directories;
- making alerts, for example, sending tickets to the Service Desk based on a request.
How does Splunk help retail cybersecurity? With it, you can minimize the impact of data breaches and fraud. You’ll understand the potential security and privacy risks, be it store devices or eCommerce websites.
You also receive information about abnormal behavior in purchases, accounts payable, points of sale, movements in the warehouse, and returns. Using this data, you will establish controls to mitigate operational and security risks.
Splunk can boast a customer base of such big corporations as Tesco, Domino’s, Nordstrom, Otto, etc.
To find out the Splunk pricing plans, you also need to contact the company representatives.
10. Trustwave
Screenshot taken on the official Trustwave website
Trustwave is another helpful security tool. It provides cybersecurity and managed security services and focuses on threat detection and response. Trustwave is a set of solutions, such as:
- managed security services with over 20 years of experience;
- cybersecurity awareness training for employees and developers;
- data protection technology. For example, a MailMarshal detection engine that analyses your email traffic.
It helps customers of 96 countries. Trustwave SSL is available for both small companies and large corporations. At the moment, anyone can purchase a suitable solution for their business or Internet project.
Trustwave provides a consolidated interface with an integrated view of your assets. You can run either self-service or managed security assessments.
It thoroughly penetrates your risk exposure and maintains an effective security program that combines prevention, proper protection, and data records.
So, it gives you the freedom to spend more time on decision-making and less time on security testing and maintenance.
You won’t find the pricing plans on the website. To do this, you need to contact the sales department.
Final Word
Any eCommerce business, be it small or medium-sized, should prioritize security in the online buying experience. Threat scenarios are continuously evolving. The amount of sensitive online data is increasing. How will you gain the trust of your customers?
By opting for an eCommerce security solution, store owners can improve their customers’ experience. Both sides of the process won’t have to worry about putting their financial security in danger or spending a fortune on security products and services. And this is the foundation for the development of your company.
About the Author
Kate Parish
Kate Parish, chief marketing officer at Onilab, with 8+ years in Digital Marketing and eCommerce web development promotion. Kate constantly upgrades her knowledge and skillset to stay fit in the progressing online world. She always does exhaustive research in such spheres as SEO, branding, SMM, PPC, and Magento PWA development, before sharing her expertise with a wide audience.